Proxies play a vital role in the digital landscape, routing internet traffic and offering a wide range of benefits from privacy protection to performance optimization.
However, selecting the right proxy type isn't the same as trying to decide on what to wear for the day.
When choosing proxies to use, you need to carefully consider various factors and be aware of the potential challenges and risks of each proxy type.
In this article, we will look at how the most common proxies are classified and what they are used for.
We will also point out the similarities and differences, so you can get a better understanding of the right proxy type to use for your specific needs.
Proxies Explained

Consider a computer program that acts as a barrier between you and the vast expanse of the internet. This program, known as a proxy, efficiently fulfills your requests with great speed.
What is its mission? To seamlessly and effortlessly connect you with the desired server. After the server performs its tasks, the proxy retrieves and delivers the requested data to you, the client.
Importance of Proxies in Today's Digital World
Proxies have become an indispensable tool in today's digital landscape. They offer a blend of enhanced privacy, security, and performance, making them vital for both individual users and organizations. Here are some of the benefits of using proxies:
- Online Privacy and Anonymity. Online privacy is a significant concern, and proxies play a crucial role in masking a user's IP address, making it difficult for third parties to track online activities.
By routing traffic through a proxy server, users can hide their actual IP address and geographic location, providing an added layer of privacy.
- Content Accessibility. Certain websites or content may be restricted in specific regions due to licensing agreements, government regulations, or other reasons.
Proxies allow users to bypass these geographical restrictions and access content as if they were in a different location.
- Bandwidth Savings and Faster Load Times. Organizations often use caching proxies to save bandwidth and accelerate web browsing.
These proxies store copies of frequently accessed web pages and serve them to users without fetching the content from the original server, leading to faster load times.
- Security and Content Filtering. Proxies can act as a shield between the user and potentially harmful content on the internet.
Organizations and institutions often employ proxies to block access to malicious websites, filter out inappropriate content, and prevent malware and phishing attacks.

- Load Balancing. In large-scale operations, multiple proxy servers can be used to distribute network traffic evenly among several servers, ensuring that no single server gets overwhelmed with too many requests.
This enhances the overall performance and reliability of the network.
- Monitoring and Logging. For businesses and institutions, proxies offer a way to monitor and log internet usage.
This can be crucial for ensuring compliance with company policies, studying user behavior, or conducting audits.
- Data Compression. Some proxies can compress inbound and outbound data, reducing the amount of data that needs to be transmitted.
This is especially beneficial for users with limited bandwidth or those accessing the internet from mobile devices.
As the digital world continues to evolve, the role and functionalities of proxies are expected to expand, further cementing their importance in the realm of internet technology.
Classifying Proxies
Proxies need to be classified for several reasons, each of which contributes to their effective and efficient use in various scenarios.
We have outlined seven classifications and the proxy types that fall under each category.
1. By Cost
Proxies can be free or paid, with each having its advantages and drawbacks. By classifying proxies based on price, users can make informed decisions that fit their budget and desired quality.
Free Proxies
Free proxies, often referred to as "web proxies," are intermediary servers that relay requests and responses between a user and the internet without any associated costs.
They are readily available on various websites and can be used without any financial commitment.
Paid Proxies
Paid proxies are IP addresses that users rent or purchase from proxy providers. They come with a cost but offer a more reliable and efficient service compared to their free counterparts.

2. By Direction
Proxies can be categorized based on the direction in which they handle requests. Both proxy types play crucial roles in ensuring smooth and secure internet operations.
Forward Proxies
Often simply referred to as a "proxy," the forward proxy acts as an intermediary between a user and the wider internet.
When a user makes a request to access a particular website or online resource, the request is first sent to the forward proxy.
The proxy then makes the request on behalf of the client to the desired destination. The response from the destination is then sent back to the proxy, which forwards it to the client.

Common Use Cases:
- Internet Access Control. Commonly used in organizations and educational institutions to control and monitor internet usage.
Forward proxies can block access to specific websites or content categories deemed inappropriate or distracting.
-
Bypassing Geo-restrictions. By routing their traffic through a proxy located in a different country, users can access content as if they were located in that country.
-
Privacy and Anonymity. Can mask the client's original IP address, providing a level of anonymity.
This can help users avoid tracking or profiling based on their IP address.
- Bandwidth Conservation. Can cache frequently accessed web content in some cases, reducing the need to fetch the same data multiple times and saving bandwidth.
Reverse Proxies
On the server side, reverse proxy servers act as an intermediate between user devices and web servers.
When a user makes a request to a web server, the request is first processed by the reverse proxy.
The proxy then determines which server to route the request to, obtains the response from that server, and returns it to the client.
The client might not even be aware of the presence of multiple servers or the reverse proxy itself.

Common Applications:
- Load Balancing. Distributes incoming client requests across multiple servers.
Ensures that no single server is overwhelmed with too much traffic, leading to optimized performance and reduced website downtimes.
- Web Acceleration. Can cache content from servers, speeding up response times.
When a user requests a cached piece of content, the reverse proxy can provide it directly without querying the backend server.
- Security and Anonymity. Adds a layer of security by masking the identity and characteristics of backend servers.
This security feature protects servers from direct exposure to the internet, reducing the risk of attacks like DDoS or direct hacking attempts.
-
SSL Termination. Handles SSL encryption and decryption, offloading the task from the web servers and ensuring efficient processing.
-
Compression. Compresses outbound data from servers to reduce the amount of data transferred between the user and server.
3. By Source
The source of a proxy refers to the origin of its IP address. This classification is crucial because the source of a proxy can determine its reliability, speed, and level of trustworthiness.

Datacenter Proxies
Datacenter proxies are artificial IP addresses provided by a secondary corporation, typically hosted on servers in data centers.
Datacenter IPs are not affiliated with an Internet Service Provider (ISP) and are not linked to a physical location.
Datacenter proxies are available in shared, private, and rotating configurations.

Residential Proxies
Residential proxies are IP addresses provided by ISPs to homeowners. They are linked to a physical location and appear as regular users to websites.
Residential proxy providers like Geonode route client traffic through residential IP addresses, which then send the connection request to the internet.

Mobile Proxies
Mobile proxies use IP addresses assigned by mobile network operators. They route traffic through mobile devices.
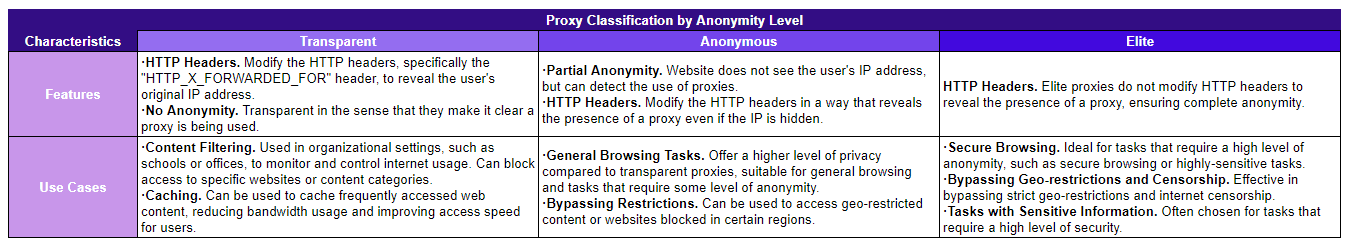
4. By Levels of Anonymity
The level of anonymity provided by a proxy is a crucial factor for many users, especially those who prioritize privacy and security.
Transparent Proxies
Transparent proxies do not hide the user's original IP address.
When a user accesses a website using a transparent proxy, the website can detect both the proxy and the user's real IP address.
Avoid using transparent proxies to access web content anonymously, because your concurrent requests are likely to be met by automatic proxy detection.
Anonymous Proxies
Anonymous proxies hide the user's original IP address but indicate that a proxy is being used.
They do not reveal the user's IP but make it clear that the connection is coming through a proxy.
Elite Proxies
Elite proxies provide the highest level of anonymity.
They hide the user's original IP address and do not give any indication that a proxy is being used.

5. By Exclusivity
The exclusivity of a proxy refers to the number of users that have access to a particular proxy IP address.
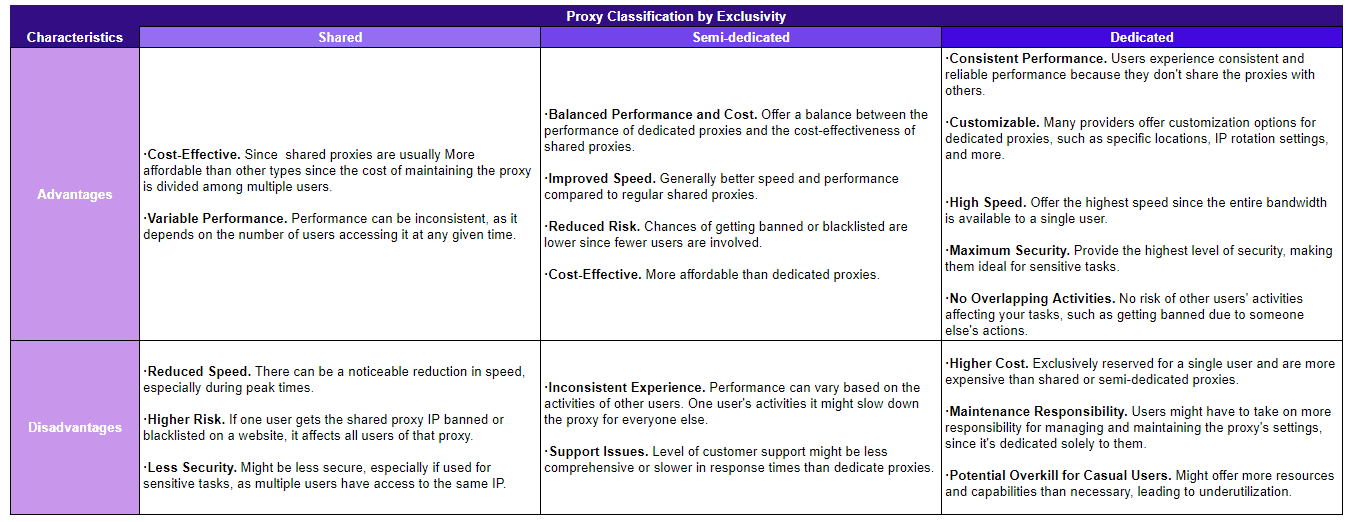
Shared Proxies
Shared proxies are used by multiple users simultaneously. This means that the same IP address is being used by several individuals at the same time.
They operate the same way as public proxies, which are free and even less reliable.

Semi-Dedicated Proxies
Semi-dedicated proxies are shared among a small group of users, typically 2-3 individuals. This ensures better performance compared to regular shared proxies.

Dedicated Proxies
Dedicated proxies, also known as private proxies, are exclusively used by a single user. No one else has access to that dedicated IP address, thanks to private networks.

6. By Rotation
Proxy rotation is a crucial aspect of proxy management, especially when dealing with tasks that involve large-scale web scraping, data extraction, or bypassing anti-bot measures.
Static Proxies
As the name suggests, static proxies provide a consistent IP address. Every time a user connects to the proxy, they will use the same IP address.
Rotating Proxies
Rotating proxies change the IP address at regular intervals or after every request. User doesn't connect with the same IP address repeatedly.
7. By Protocol
The protocol used by a proxy determines how data is transmitted between the client and the server.
Different protocols offer varying levels of security, speed, and functionality. Here's a breakdown of some common protocol-specific proxy types:
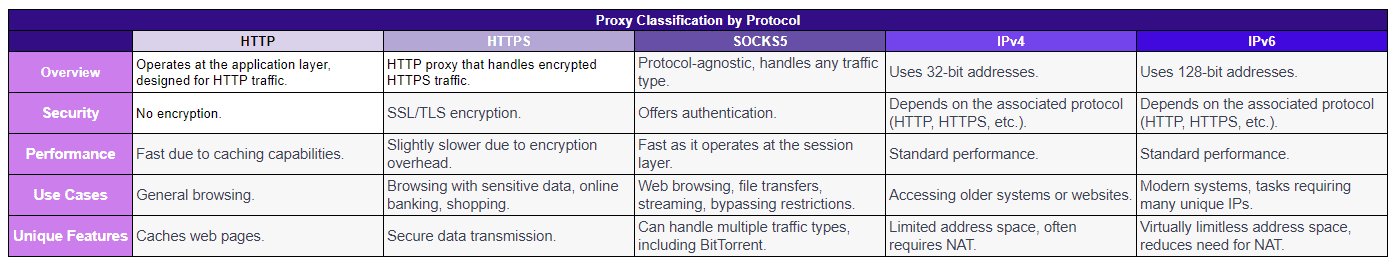
HTTP & HTTPS Proxies
HTTP proxies operate at the application layer of the OSI model and are specifically designed to interpret and forward HTTP traffic.
They can cache web pages and offer faster response times for frequently accessed websites.
HTTPS handle encrypted HTTPS traffic. They ensure secure data transmission by using SSL/TLS encryption.
- Differences - HTTPS proxies encrypt the data between the client and the proxy, making it difficult for eavesdroppers to understand the transmitted data.
HTTP proxies, on the other hand, do not encrypt the data, making them less secure.
-
Use Cases - HTTP proxies are suitable for general browsing, while HTTPS proxies are ideal for tasks that involve sensitive data, like online banking or shopping.
-
Setup - Setting up an HTTPS proxy might require additional steps, like installing an SSL certificate, compared to an HTTP proxy.
SOCKS5 Proxies
Unlike HTTP/HTTPS proxies that handle specific types of traffic, SOCKS5 proxies can handle any type of traffic, be it HTTP, HTTPS, FTP, or even BitTorrent.
-
Security - SOCKS5 proxies offer a level of authentication, ensuring that unauthorized users cannot access the proxy.
-
Performance - They operate at a lower level (session layer) of the OSI model, which can lead to faster data transmission since there's no need to interpret the data.
-
Advantages - Can handle a variety of tasks, from web browsing to transferring files or even streaming.
-
Bypass Restrictions - Their ability to handle different types of traffic makes them ideal for bypassing internet restrictions or geoblocks.
-
Enhanced Privacy - With authentication and a lack of data interpretation, SOCKS5 proxies offer a higher level of privacy compared to HTTP proxies.
IPv4 vs. IPv6 Proxies
- Address Length - IPv4 uses 32-bit addresses, resulting in approximately 4.3 billion unique addresses.
IPv6, on the other hand, uses 128-bit addresses, offering a virtually limitless number of unique addresses.
- Compatibility - Many modern systems and websites support both IPv4 and IPv6, but some older systems might only support IPv4. NAT (Network Address Translation).
IPv4 often requires NAT due to the limited number of available addresses. IPv6, with its vast address space, reduces the need for NAT, allowing devices to have unique global addresses.
- Use Cases - IPv4 Proxies are ideal for accessing older systems or websites that do not support IPv6.
They are also more common and widely used. IPv6 Proxies are suitable for modern systems and future-proofing, given the growing adoption of IPv6.
They can also be beneficial for tasks that require a large number of unique IP addresses, like web scraping.
Choosing the Right Proxy
Now that you know the different types of proxies, you can make better informed decisions about the proxy type to use for your specific needs.
- Purpose of the Proxy. Identify the primary reason you need a proxy.
Are you looking to scrape data, manage social media accounts, verify ads, or bypass geo-restrictions? The purpose will guide your choice.
- Anonymity Requirements. How important is it for your activities to remain undetected?
If high anonymity is crucial, residential or mobile proxies might be more suitable than datacenter proxies.
-
Geographical Needs. If you need to access content or services restricted to specific regions, ensure the proxy provider offers IPs from those locations.
-
Volume and Scalability. Consider the volume of requests you'll be making.
If you're handling large-scale operations, you might need a provider that offers a large pool of IPs or rotating proxies.
- Budget Constraints. While it's essential to get a proxy that meets your needs, it's equally important to consider how much you're willing to spend.
Evaluating Different Proxy Providers

- Reputation and Reviews. Research potential providers and read reviews from other users.
A provider with a strong reputation in the industry is often more reliable. Geonode offer proxy services that
-
Type of Proxies Offered. Ensure the provider offers the type of proxy you need, be it datacenter, residential, or mobile.
-
Customer Support. Opt for providers with robust customer support. Issues with proxies can arise, and having a responsive support team can be invaluable.
-
Pricing and Packages. Compare the pricing structures of different providers. Some might offer discounts for bulk purchases or longer commitments.
-
Terms of Service and Usage Policies. Review the provider's terms of service to ensure they align with your intended use.
Some providers might have strict usage policies or might not allow certain activities.
Testing Proxy Performance
- Speed Tests. Once you've chosen a proxy, test how fast your internet connection as you use it.
While datacenter proxies are generally faster, it's essential to ensure that residential and mobile proxies meet your speed requirements.
- Anonymity Checks. Use online tools to check if your IP is leaked or if the proxy is detectable while you do various internet activities.
Doing so will give you an idea of the anonymity level the proxy provides.
-
Geolocation Verification. If accessing content from specific regions, verify that the proxy's IP is genuinely from that location.
-
Uptime and Reliability. Monitor the proxy over a period to check its uptime. A good proxy should have minimal downtime.
-
Rotation and Pool Size. If you're using rotating proxies, test how often the IP changes and the diversity of the IP pool.
This is crucial for tasks that require a fresh IP for each request.
Choosing the right proxy is a combination of understanding your specific needs, thoroughly evaluating potential providers, and rigorously testing the chosen proxy's performance.
By following these steps, you can ensure that you select a proxy that aligns with your objectives and provides a seamless browsing experience.
Wrapping Up
Proxy networks have emerged as indispensable tools, bridging gaps, ensuring online security, providing protection from attacks, and optimizing performance.
Whether it's for data scraping, ad verification, or simply maintaining online privacy, the right proxy can make a significant difference.
The efficacy of these tools is not just in their individual capabilities but in their alignment with the user's specific needs. A mismatch can lead to inefficiencies, increased costs, or even potential bans. Thus, the emphasis on choosing the right proxy cannot be overstated.
Proxy networks and proxy protocols like many facets of technology, are ever-evolving. As digital challenges grow and diversify, so do the solutions.
Proxy service providers like Geonode offer a great choice for people, enhancing features and making innnovations not just to improve connection speeds but also to provide users with a greater sense of security.
For individuals and businesses alike, staying updated and continuously learning about the latest developments of proxy software is not just beneficial — it's essential.
By doing so, you can harness the additional features and the full potential of proxy online services, ensuring optimal performance, security, and adaptability in an increasingly digitalized world. Embrace the journey of knowledge in this dynamic field, and let it guide you to smarter, more informed decisions in all your digital endeavors.



















